Services

Firmware services
- Memory chip readout/copying
- Readout protection bypass
- Disassembly and annotation
- Memory/peripheral mapping
- Firmware blob modification
- Protocol reverse engineering
- Firmware reimplementation

Hardware services
- Component identification
- Schematic and PCB re-engineering
- Hardware modification and retrofitting
Project Portfolio
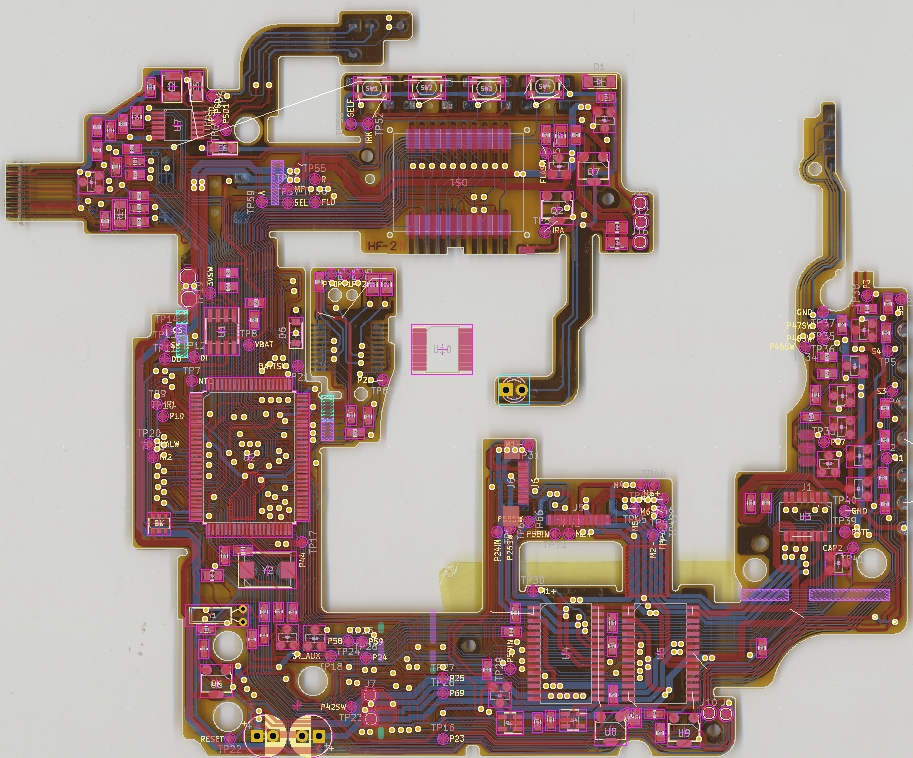
Konica Hexar AF Flex-PCB
One of the best compact analog cameras ever made - and also one that unfortunately suffers from leaky capacitors that cause massive corrosion of a very complex flex PCB. While some cameras can be saved if the capacitors are replaced in time, many have extensive corrosion damage after 20-30 years of use and require a replacement PCB if they are to continue to work. I have taken up the complex but rewarding work of recreating the entire flex PCB design, along with schematics and documentation that will (hopefully) aid people in fixing their precious cameras.
Nikon Coolscan Adapter Unlock
While no longer manufactured nor supported, the famous Nikon Coolscan dedicated film scanners remain one of the best, most affordable options for digitizing negatives. Years ago, Nikon decided to segment the market by artificially disallowing the "lower" models from scanning entire rolls of film - despite the hardware having perfect capability to do it. My modification removes adapter ID checks from the firmware - which, together with cutting a hole in the back of the device, effectively upgrades its batch scanning capability to that of a professional lab scanner, taking entire 36 exposure rolls at once.
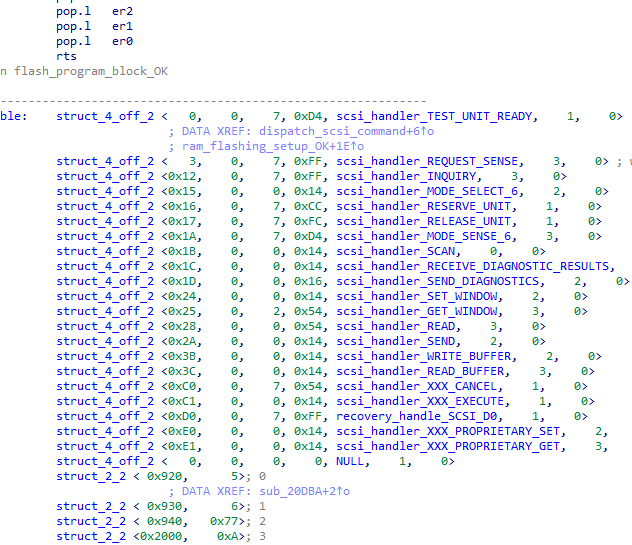
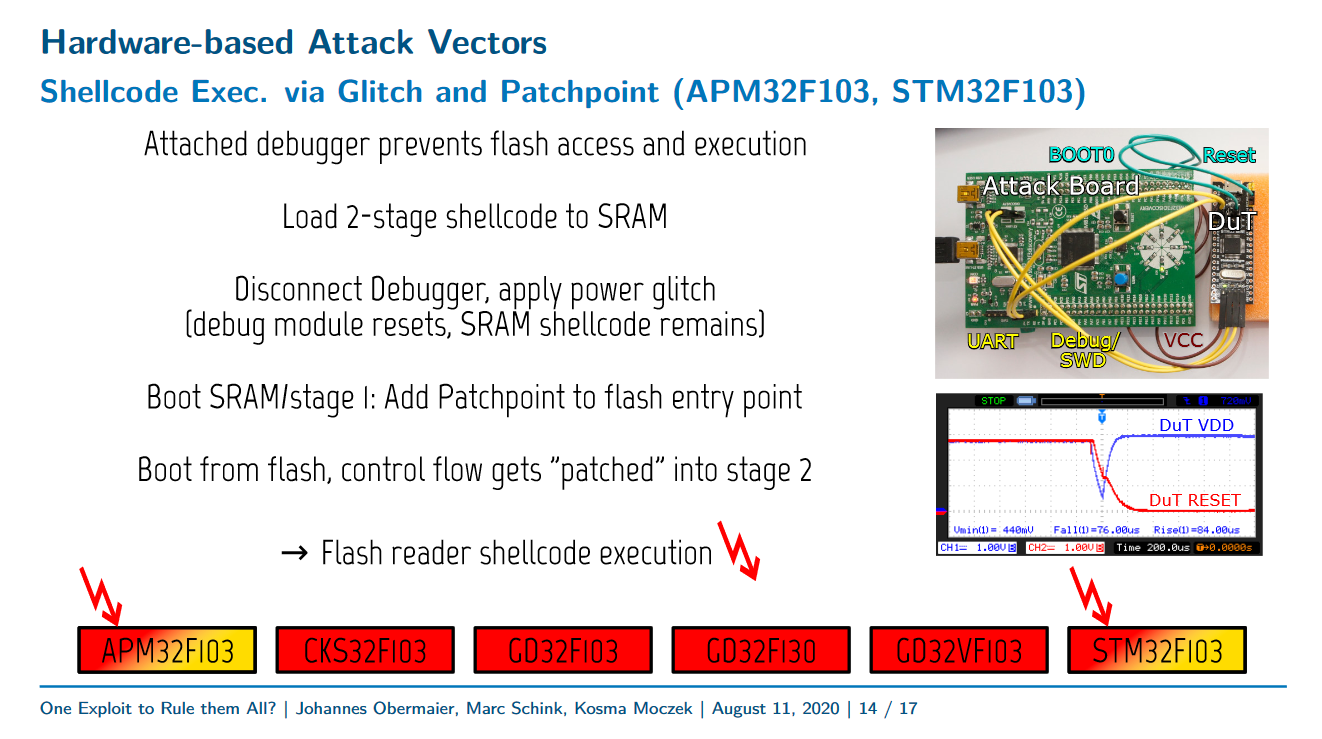
STM32F1 Readout Protection Bypass
I have created a three stage exploit-chaining payload that, combined with hardware glitching, allows for bypassing RDP on all STM32F1 devices (and some counterfeits/clones). The main exploit uses a novel self-debugging technique that's potentially useful against all ARM devices utilizing the standard Cortex-M FPB unit. The glitcher/debugger board has been affectionally dubbed stm32f1uck, for STM32F1 Unauthorized Copying Kit. The complete setup can be read about in the USENIX WOOT 20 paper.